- (888) 764-0688
- [email protected]
- 24-hour Phone Support

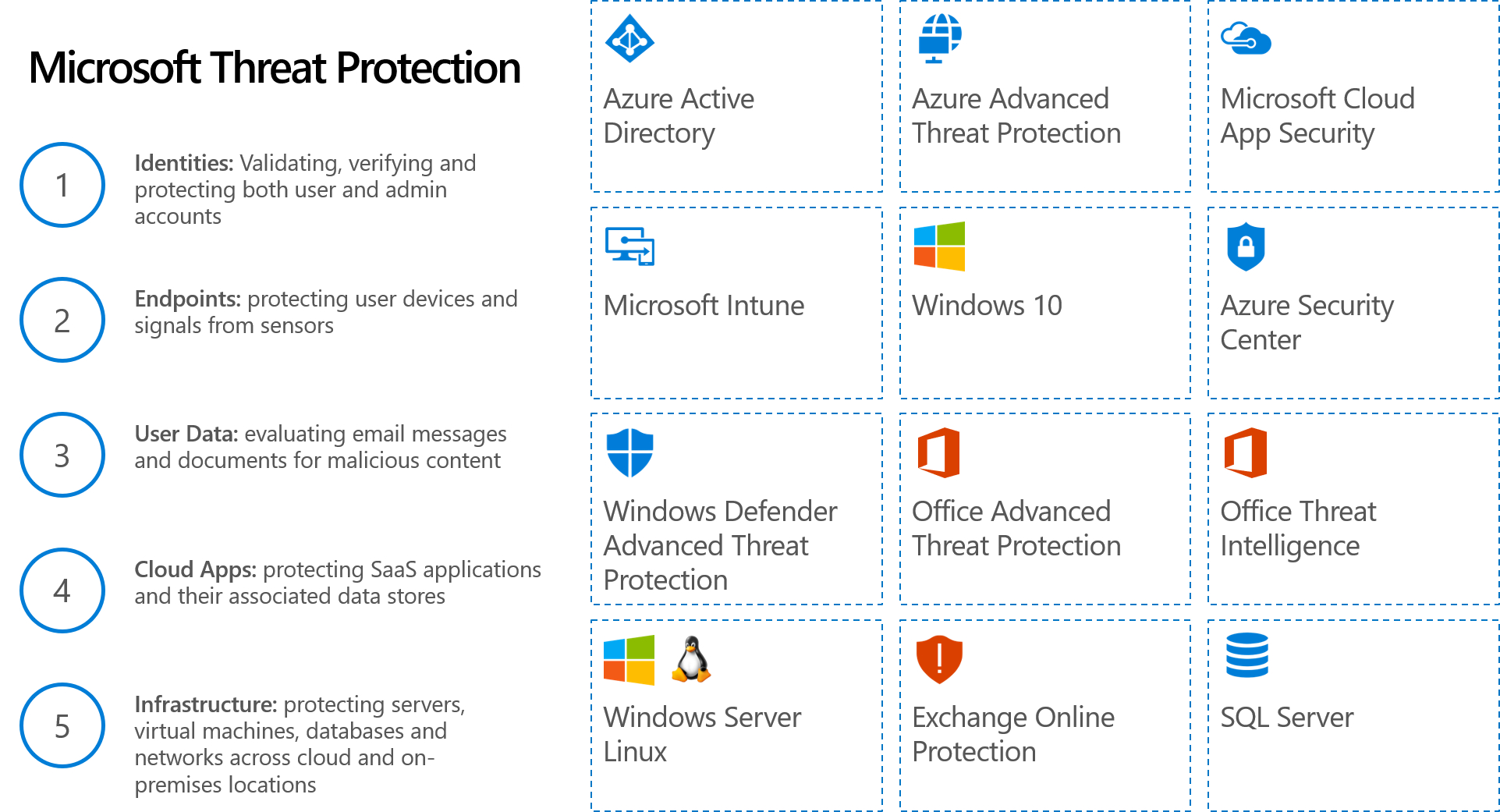
As more of the workforce connects from their homes, there has been a spike in usage for remote productivity services. Many organizations are giving Microsoft Office 365 subscriptions to all of their staff, using more collaboration tools from Outlook, OneDrive, SharePoint, and Teams.
Unfortunately, this is creating new security vulnerabilities with more untrained workers being attacked by malware or ransomware through attachments, links, or phishing attacks.
This article will provide you with an overview of how Microsoft Office 365 Advanced Threat Protection (ATP) can help protect your organization, along with links to help you enable each service.
ATP is included in the Microsoft Office 365 Business Premium, Enterprise E5, and Education A5 subscriptions, but it can be added to almost any subscription.
Microsoft Office 365 ATP helps your users determine if a link is safe when using Outlook, Teams, OneNote, Word, Excel, PowerPoint and Visio. Malicious or misleading links are a common method for hackers to direct unsuspecting users to a site that can steal their information. These emails are often disguised to look like they are coming from a manager or the IT staff within the company. ATP will automatically scan links in emails and cross-reference them to a public or customized list of dangerous URLs. If a user tries to click on the malicious link, it will give them a warning so that they understand the risk if they continue to visit the website.
One of the most common ways which your users will get attacked is by opening an attachment that is infected with malware. When the file is opened, it could execute a script that could steal passwords or lock up the computer unless a bounty is paid, in what is commonly known as a ransomware attack. ATP will automatically scan all attachments to determine if any known virus is detected. You and your users will be notified about anything suspicious to help you avoid any type of infection.
When ATP anti-phishing is enabled, all incoming messages will be analyzed for possible phishing attacks. Microsoft Office 365 uses cloud-based AI to look for unusual or suspicious message elements, such as mismatched descriptions, links, or domains. Whenever an alert is triggered, the user is immediately warned, and the alert is logged so that it can be reviewed by an admin.
Approved users will have access to the ATP dashboard along with reports about recent threats. These reports contain detailed information about malware, phishing attacks, and submissions. A Malware Status Report will allow you to see malware detected by type, method, and the status of each message with a threat. The URL Protection Status Report will display the number of threats discovered for each hyperlink or application and the resulting action taken a user. The ATP Message Disposition report shows the different types of malicious file attachments actions in messages. The Email Security Reports include details about the top senders, recipients, spoofed mail, and spam detection.
How to view all the various ATP reports. Note: there are some more advanced reports which must be triggered through a PowerShell cmdlet.
Another important component of ATP is the Threat Explorer which allows admins or authorized users to get real-time information about active threats in the environment through a GUI console. It allows you to preview an email header and download an email body, and for privacy reasons, this is only permitted if permission is granted through role-based access control (RBAC). You can then trace any copies of this email throughout your environment to see whether it has been routed, delivered, blocked, replaced, failed, dropped, or junked. You can even view a timeline of the email to see how it has been accessed over time by recipients in your organization. Some users can even report suspicious emails and you can use this dashboard to view these messages.
Microsoft Office 365 leverages its broad network of endpoints to identify and report on global attacks. Administrators can add any Threat Tracker widgets which they want to follow to their dashboard through the ATP interface. This allows you to track major threats attacking your region, industry, or service type.
Another great security feature from Microsoft Office 365 ATP is the ability to automatically investigate well-known threats. Once a threat is detected, the Automated Incident Response (AIR) feature will try to categorize it and start remediating the issue based on the industry-standard best practices. This could include providing recommendations, quarantining, or deleting the infected file or message.
One challenge that many organizations experience when developing a protection policy is their inability to test how their users would actually respond to an attempted attack. The ATP Attack Simulator is a utility that authorized administrators can use to create artificial phishing and password attacks. These fake email campaigns try to identify and then educate vulnerable users by convincing them to perform an action that could expose them to a hacker. This utility can run a Spear Phishing Campaign, Brute Force Attack, and a Password Spray Attack.
How to enable the ATP Attack Simulator
This diverse suite of tools, widgets, and simulators can help admins protect their remote workforce from the latest attacks. Microsoft has taken its artificial intelligence capabilities to learn how millions of mailboxes are sharing information, and use this to harden the security of their entire platform.
Did you know Microsoft does not back up Office 365 data? Most people assume their emails, contacts and calendar events are saved somewhere but they’re not. Secure your Office 365 data today using LG Networks Office 365 Backup – the reliable and cost-effective mailbox backup, recovery and backup storage solution for companies and MSPs.
